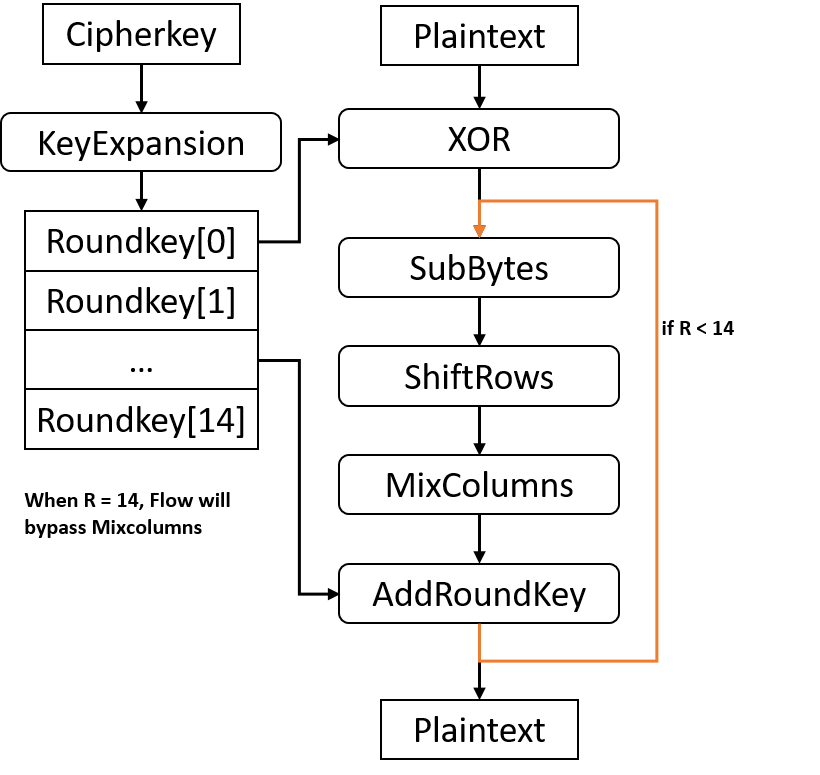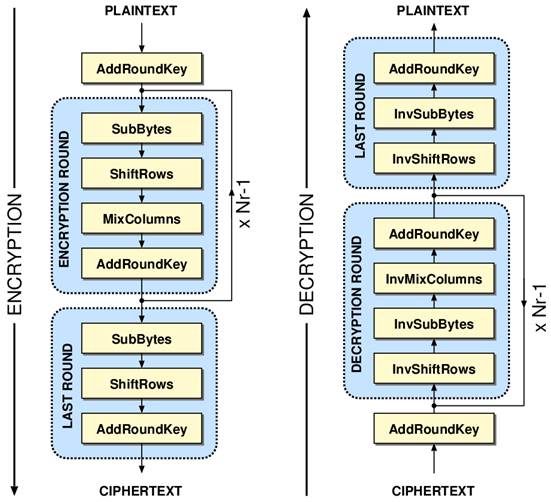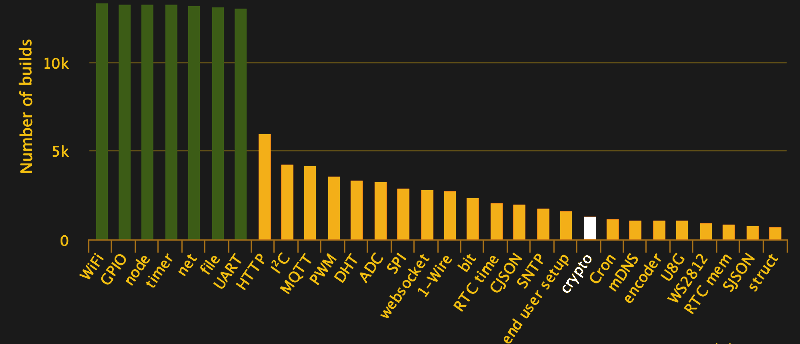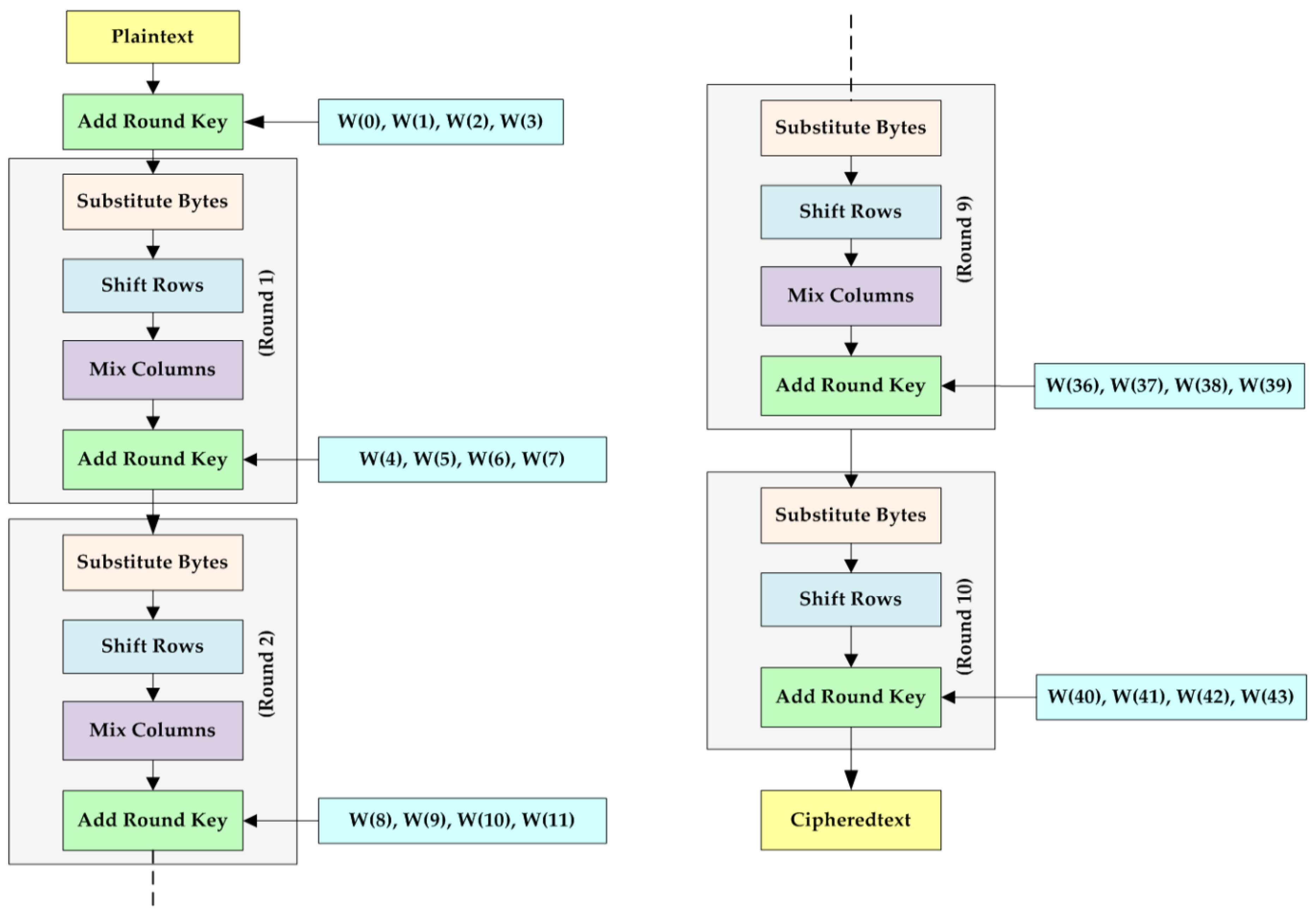
Electronics | Free Full-Text | 10 Clock-Periods Pipelined Implementation of AES-128 Encryption-Decryption Algorithm up to 28 Gbit/s Real Throughput by Xilinx Zynq UltraScale+ MPSoC ZCU102 Platform | HTML

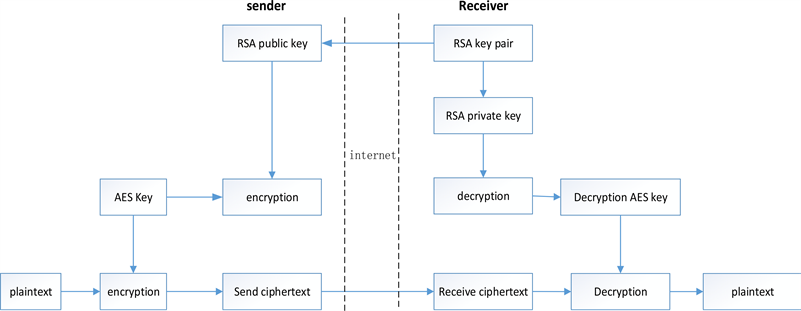
AES Encryption 256 Bit. The encryption standard to rule them… | by Cory Maklin | Towards Data Science
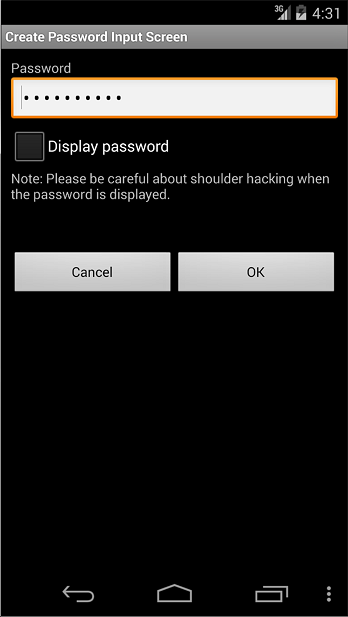
5. How to use Security Functions — Android Application Secure Design/Secure Coding Guidebook 2022-01-17 documentation
aes-128-cbc encryption with 32 byte key and 16 byte IV failing with "Invalid Key length" · Issue #27622 · nodejs/node · GitHub
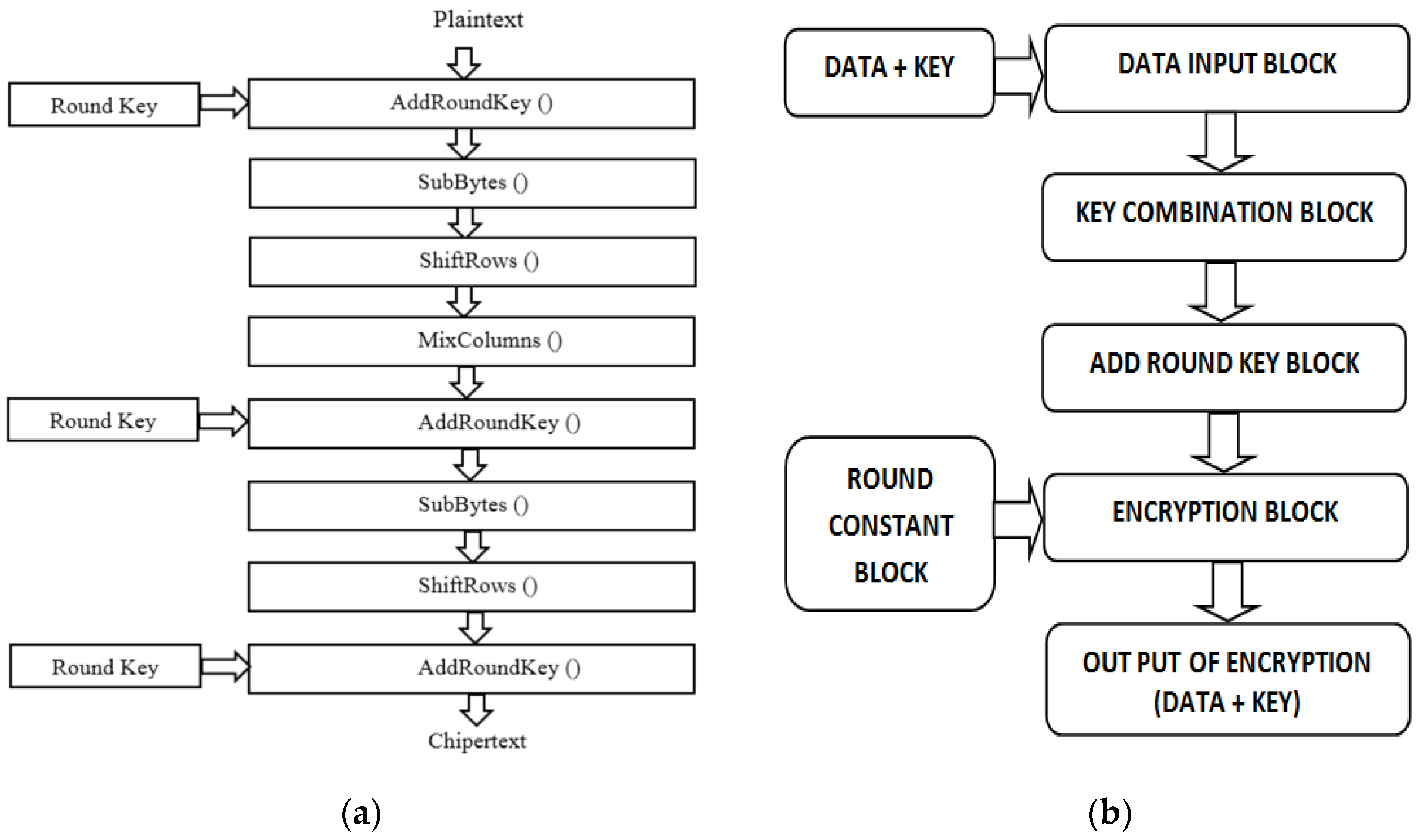
Electronics | Free Full-Text | 10 Clock-Periods Pipelined Implementation of AES-128 Encryption-Decryption Algorithm up to 28 Gbit/s Real Throughput by Xilinx Zynq UltraScale+ MPSoC ZCU102 Platform | HTML

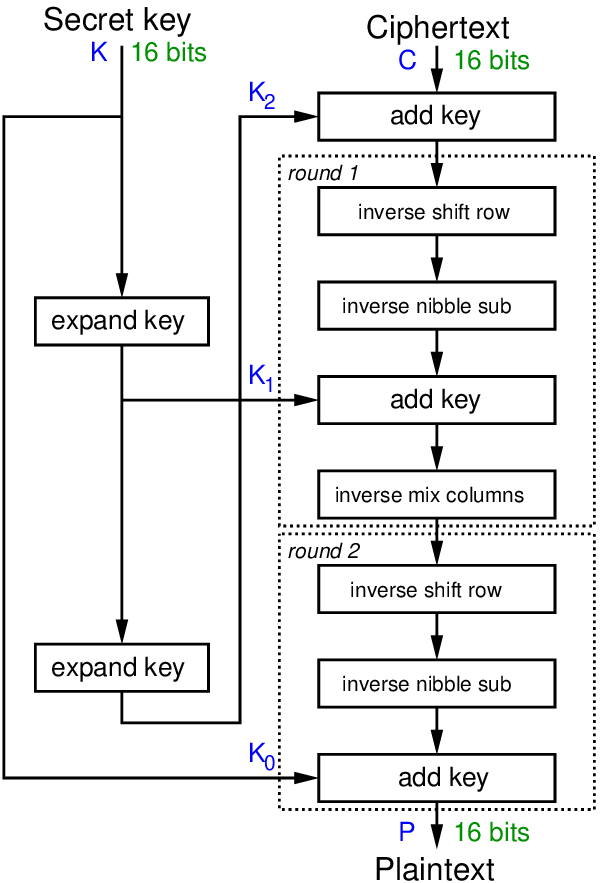
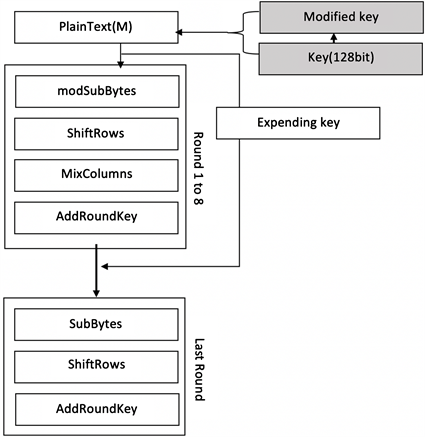
PDF) Security enhancement of Advanced Encryption Standard (AES) using time-based dynamic key generation
53 Gbps Native GF(2 Composite-Field AES-Encrypt/Decrypt Accelerator for Content-Protection in 45 nm High-Performance Microproces